In this age of digital information, things can happen instantaneously as long as you are online.
Connecting to people, keeping up on current events, e-commerce, as well as financial transactions, can happen with a few taps and swipes on your screens.
Nowadays, being connected is like entering a gateway to an information surplus and there is almost no limit to the knowledge and data that you can tap on and tasks you can perform.
However, have you ever thought about the sensitivity of the information you’re sharing on the internet and how secure the platforms are that houses your personal data?
Considering how catastrophic getting hacked can be for companies, you need to make sure that you’re personal information are in good hands.
The Need for Cybersecurity
Cybersecurity is a threat faced by businesses with online footprints — no matter how big or small.
In 2017, an average of 130 security breaches was observed and it is projected to increase by about 27.4% annually.
Emphasis on this is highlighted due to the cost of mitigating issues should a breach take place.
According to the same study, an average cost of 2.4 million USD is spent by companies in order to recover from such attacks and the ordeal usually lasts 50 days before it is resolved.
Can you imagine how adverse the impact of cyber threats is to businesses, consumers, and the like?
In situations like these, nobody wins.
To help you avoid such scenarios, let’s look into the most common cybersecurity threats and how you can overcome them.
Common Cybersecurity Threats
Ransomware is malicious software that locks you out of your files and computer programs or threatens to publish your personal data unless a payment, or a ransom, is made.
In the past, payments are demanded through the mail. Nowadays, they are settled through cryptocurrencies such as Bitcoin.
Such threats can be prevented through the use of Anti Malware software that can be downloadable for free in limited functionalities.
Phishing of information happens when data or information is obtained by means of deception, either through a bogus website or email (among other means).
Normally, an email is sent to individuals that require them to log in to a specific link that would further ask for their personal information.
This then leads to the exposure of sensitive data to the people who are trying to obtain them. Personal information such as passwords and credit card numbers are usually at risk.
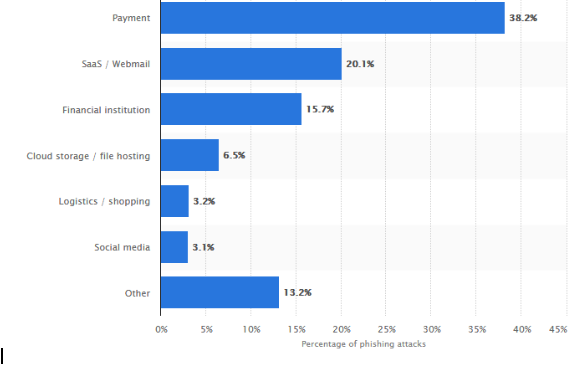
A study by Statista indicated that in 2018, 38% of attacks targeted payment services and 16% targeted financial Institutions.
This cybersecurity threat is best overcome with mindfulness and awareness.
Oftentimes, you will get an email with suspicious links, or the sender asking for information. If you think something doesn’t add up, be sure to check the link and make the necessary inquiries.
For example, your name is not mentioned in the email and you are only referred to as a “Valuable Customer” and your email address is indicated in bcc.
Sometimes you are routed to a website that looks like the authentic login pages but is published in unsecured servers.
DoS (Denial of Service) attack takes place from a single computer running DOS tools in your network to overload and blocks your network.
On the other hand, DDoS (Distributed Denial of Service) attack happens on a larger scale, often by computers rounded up to overload your system altogether to block your network.
Stated plainly, both attacks target your system and disrupt it with massive amounts of data until nobody can connect to it.
A firewall is a good line of defense since they are effective in warding off the virus from entering your network.
Keep in mind that such attacks come with a cost. As of April 2018, there were documented financial damages to businesses ranging from less than 100,000 USD to more than 5 million USD.
As per Statista’s studies, 53% of attacks caused financial damages of at least half a million USD.
While there is a long list of available software that you can use to help you against cyber attacks, nothing beats working with a savvy, third-party cybersecurity provider.
When you employ the help of third-party cybersecurity companies, you have a dedicated group of highly-skilled professionals who are constantly monitoring your network 24/7, to strengthen your defenses against cybercriminals who are attempting to infiltrate your network.
Some of the crucial cybersecurity features that you can enjoy when working with third-party cybersecurity providers are:
- DDoS Mitigation: The company diverts or routes the high-traffic to its mitigation platforms. They then filter out the good traffic from the bad, then directing only the good traffic to your site.
- Insurance Network Testing: The company uses all the tricks and strategies used by real hackers to uncover the weak areas of your network through a wide range of penetration testing methods.
Of course, these are just some of the many crucial benefits security companies can offer to protect you against the threats.
With how cybercriminals are constantly coming up with new strategies to compromise your network, you need the help of cybersecurity professionals
Conclusion
While some companies aren’t as keen on protecting their sites against cyber attacks, you shouldn’t make the mistake of doing the same.
The fact is, if you are dead serious about taking your business to greater heights, you can’t afford to slack off on your cybersecurity.
The good news is, the steps you can take to protect yourself against the attacks isn’t rocket science either. You can run training sessions to teach your team about the dos and don’ts of cybersecurity, you can subscribe to tools that can help fortify your cyber defenses, or you can work with third-party cybersecurity companies to make sure that professionals are on your case, constantly protecting your company against cyber attacks.
If you have questions, suggestions, or ideas that you’d like to share about cyber attacks and how to overcome them, feel free to share your ideas in the comments section below. Cheers!